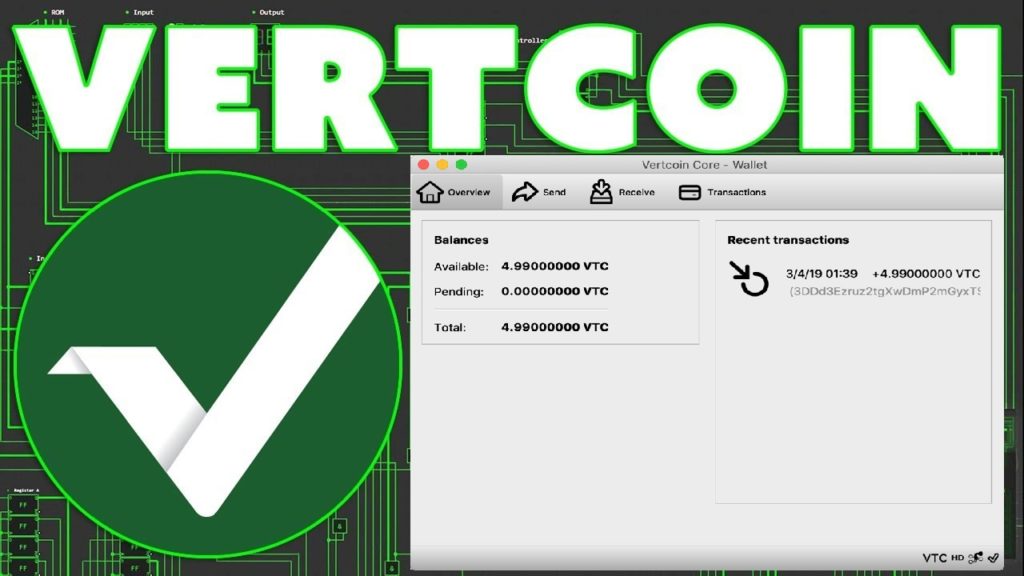
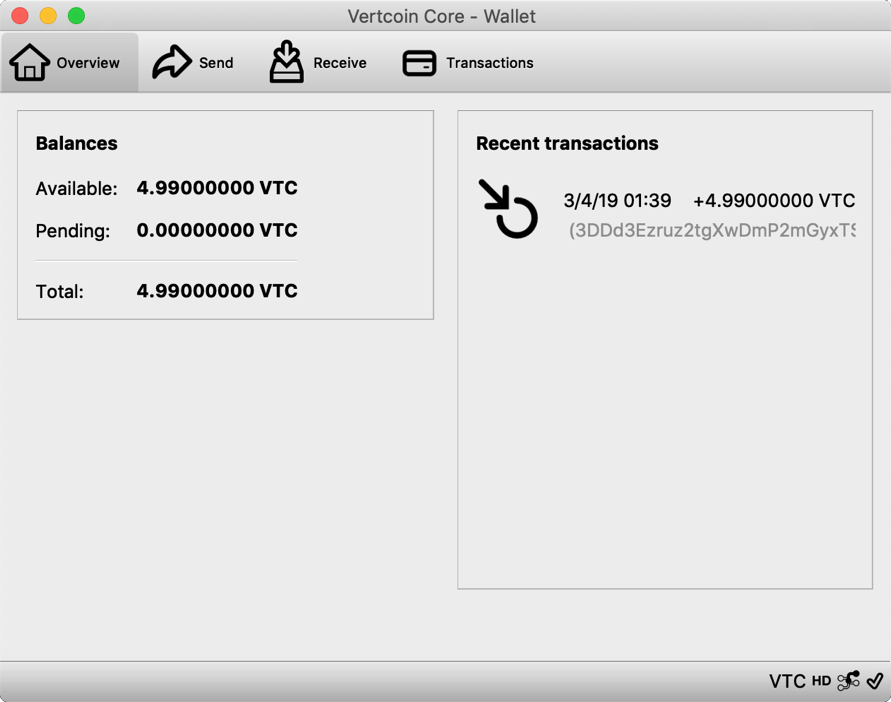
Vertcoin Core – VTC Wallet
Vertcoin is a fork of bitcoin designed to counter the monopolization of mining. According to the company’s website, “Vertcoin is a decentralized currency owned by its users,” a P2P cryptocurrency similar to Bitcoin and Litecoin. Like its two predecessors, Vertcoin exists solely as a currency and uses proof-of-work (PoW) to achieve distributed consensus.
However, unlike its two predecessors, Vertcoin aims to preserve decentralized mining functions, so unlike most PoW coins, it is ASIC-resistant. Calling its project a “people’s coin,” the Vertcoin team believes that ASIC resilience provides a fairer and more democratic currency for users and miners alike. To that end, Vertcoin uses its own “1-click” miner, a program designed to make mining more accessible to the general public. So what makes Vertcoin work, and how can it guarantee ASIC resilience?
How Vertcoin works
The thing about Vertcoin is that it completely bans miners from using ASIC equipment to mine its blockchain. This means that Vertcoin takes us back to the good old days when mining only required a decent video card or computer processor. Of the other pluses and advantages of VTC, the following can be highlighted:
- 2.5 minute blocks
- subsidy halved after 840,000 blocks (~4 years)
- ~84 million coins
- 25 coins per block
- Difficulty retargeting each block to recover from large hash rate fluctuations
- Verthash proof-of-work algorithm for ASIC resistance
- Vertcoin’s philosophy of ASIC sustainability:
“When Vertcoin first started in 2014, it used the Scrypt-N algorithm to achieve PoW consensus. Since then, Scrypt-N-specific ASICs have emerged, so the Vertcoin team had to start from scratch. When they succeeded, they created the Lyra2RE algorithm, forking Vertcoin on December 13, 2014 to update the core software. According to Lyra2RE, the new algorithm allowed the team to “alter memory usage and time costs independently, giving [them] more leverage against ASIC.”
- The team continues to explain Lyra2RE’s resilience to ASIC to the end of the white paper:
“Unlike Scrypt-N, the time and memory costs are separated, giving us independent control over both parameters. The ASIC was much easier to design for Scrypt-N than for Lyra2RE, because increasing Scrypt’s N-factor simply means doing more iterations of the algorithm. In Lyra2, while the increase in timing is only due to the increased number of iterations, the increased memory requirements mean that any potential ASIC device must be physically designed with more memory for each thread. In the future, if ASICs are ever designed for Lyra2RE, we will simply have to move to higher memory requirements and those ASICs will no longer function properly.
After implementing Lyra2RE, the team upgraded to Lyra2REv2 with another hard fork on August 10, 2015. This upgrade was necessary because the botnet had seized control of 50 percent of the network’s hash power. For now, Lyra2REv2 allows you to keep ASIC miners at bay. Thus, the only suitable hardware for mining is either GPUs or CPUs.
Download the VTC Wallet to get the wallet address
1. If the above link isn’t available, you can put up an agent or download the link I shared. Link:
2. Run the installation according to the instructions, specify the directory to install, if you do not need more information, you can check to save only the latest 2GB data.
3. After you click “OK” this is a relatively long process waiting for installation (a really long time, it will stay in the installation interface for a long time without any movement, and remember to close the anti-virus software, otherwise it will be blocked), after the installation is completed the Long block synchronization will start, maybe 5GB.
4. But when the block is synchronized, we can already create a payment address, first click on the synchronization progress of the hidden block, then click “get”, click “new payment address”, you can immediately see your payment address QR code and payment address.
5. When the wallet is still in block synchronization mode, you can first discard the mining tools.
Download Vertcoin Wallet (Verthash)
Read more articles about cryptocurrencies and mining at CRYPTO-WALLETS.ORG.
The Telegram channel about cryptocurrency and mining Bitcoin, Ethereum, Monero and other altcoins:
-
Wallets for TON. TonKeeper, Tonhub, MyTonWallet, Wallet.TG
Краткий обзор кошельков TON, которые вам необходимы для начала работы с этой новой быстро развивающейся сетью блокчейна! (TonKeeper, Tonhub, MyTonWallet). Кошельки TON разработаны для взаимодействия с реестром блокчейна TON и позволяют пользователям управлять своими активами и совершать транзакции в сети. Кошельки TON упаковывают сложные инструкции в простые щелчки, позволяя любому человеку использовать и исследовать сеть, сохраняя при этом полное владение своими активами в блокчейне.
-
Overview of decentralized crypto platforms Waves
The Waves team is developing tools to create a decentralized technology segment that will become the basis of Web 3.0 – the digital landscape of the future.
-
Review of the best wallets for Litecoin (LTC)
Like Bitcoin, the Litecoin cryptocurrency is rapidly gaining momentum and becoming quite a sought-after digital asset around the world.